Table of Contents Overview
Cirrus OrgBrandedID Documentation
Table of Contents
1. Overview
Overview
Cirrus’ OrgBrandedID is a SAML compliant identity provider with a lightweight registration capability. To create an external identity, the end user provides a name, email address and any custom data required. The Registration process validates the email address and collects a password that meets the policies of the organization.
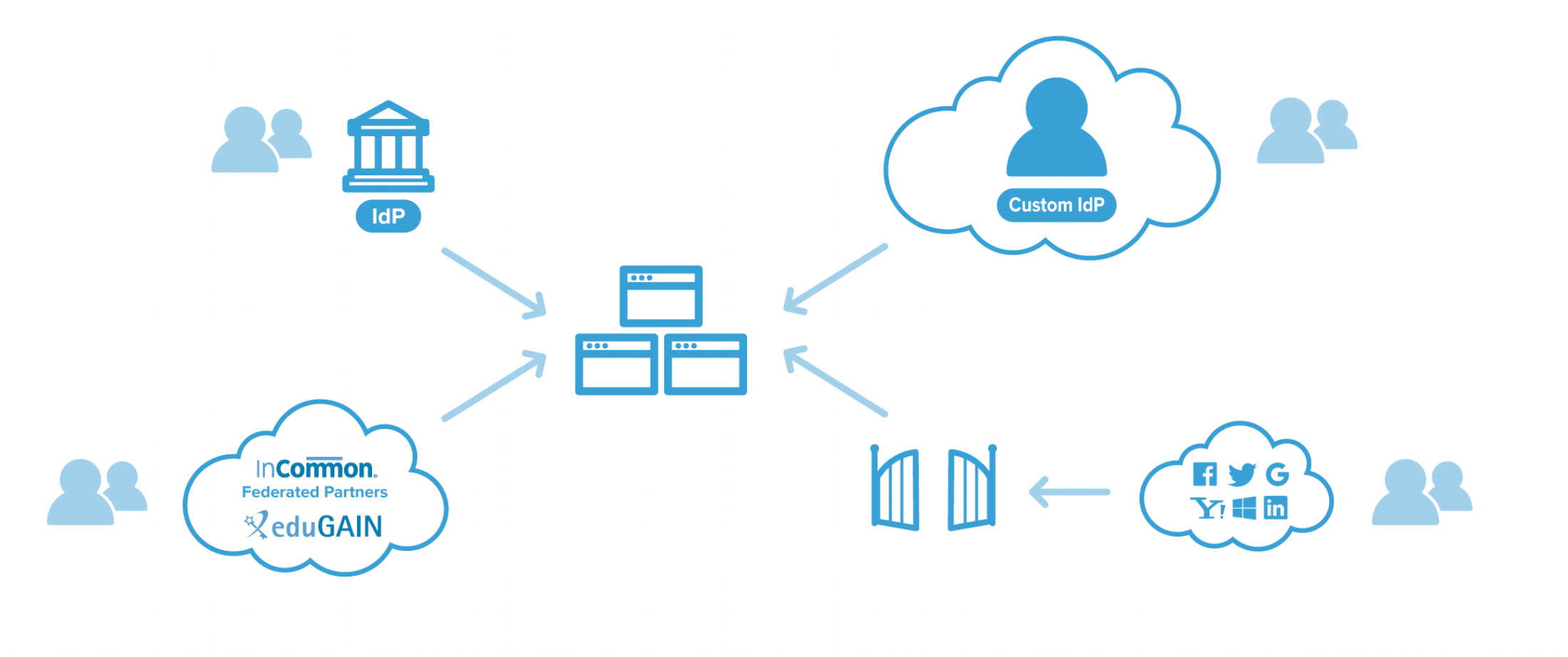
Once registered, the identity can be used for accessing any SAML service provider (or CAS with the Cirrus Proxy service) as illustrated in the diagram below.
- End users can create an account in the OrgBrandedID (upper right) to access enterprise applications (in the middle)
- The OrgBrandedID can be a peer with other federated SAML identity providers
- Easily configurable to reflects the organization branding and credential policies
- Integrated into both the Cirrus Identity Invitation and Account Linking solutions
Common Uses

